Risk assessments are critical to business functions across the board. Learn what OSINT methodology and dozens of resources can bring to improving risk management.
Our world is rapidly becoming fully digital, generating massive amounts of publicly available data daily. Understanding how to leverage this data effectively is crucial for businesses to survive today's complex threat landscape and make correct business decisions.
Online data holds valuable insights about potential threats to your business. By understanding how to collect and analyze it, you can proactively identify and mitigate these threats before they cause problems to your operations and/or impact your business reputation and, consequently, profits.
In this guide, I will suggest a methodology to utilize open-source intelligence (OSINT) in business risk management and suggest many tools, online resources and search techniques to get the information you need more quickly and efficiently.
Methodology for using OSINT in risk assessment
An OSINT search methodology will provide a structured and systematic approach to gathering, analyzing and verifying publicly available data. The methodology will allow your organization to focus on the most important sources and information and avoid wasting time collecting and analyzing irrelevant information.
Define your search objectives
The first thing we need to do is define our search objectives; this allows us to identify the main routes of our search. In this step, the main question will be:
Who is our target? Or for whom are we making this risk assessment study?
Our target could be:
- A business
- Government agency
- Healthcare organization
- Manufacture
- Financial or educational institutional
- Public utilities companies, such as transportation, energy or water supply company
- Nonprofit organization
Identify the type of risks we are concerned about
Each organization may be subject to different risks according to its industry, type of operations or other external factors, such as as its location. For instance, are we concerned with collecting risk information related to:
- Financial – such as market risk, credit risk, liquidity risk, counterpart credit risk, regulatory and compliance risk, currency risk, interest rate risk and operational risks
- Reputation – includes data breaches and privacy violations, corporate governance failures, product/service quality issues, negative media coverage and public perception, social responsibility issues, workplace culture and employee relations issues
- Operational – such as business process failure, IT problems, disruption in supply chain networks, workforce shortages, compliance and regulatory risks, disaster recovery risks and third-party vendors risks
- Technology – such as cybersecurity threats; data breaches; cloud computing risks; insider threats; third-party vendors risks (e.g., using malicious or vulnerable software components); using legacy systems and outdated software; internet of things (IoT) and mobile device security risks; compliance and regulatory risks when failing to comply with relevant data protection and privacy laws
- Human resources – include any risk or challenges associated with an organization's workforce, such as talent acquisition challenges, workplace conflict and misconduct
- Compliance risks include any dangers or challenges that arise from failing to adhere to applicable laws, regulations and industry standards
- Strategic risks to business – such as competitive and innovation risks
- Geopolitical risks – such as political instability and regime change, trade wars, sanctions rules and export controls, cyber warfare, terrorism and global health risks (such as the COVID-19 pandemic)
The type of information we need to gather
In this step, we need to identify the data sources we will use during our research. Here are the primary data source categories that we can leverage.
Financial data
Financial data about enterprises include all business information about companies that reveal their financial health, performance and operations. This data can be obtained from various sources. Here are the main ones:
- The Electronic Data Gathering, Analysis, and Retrieval system (EDGAR)
- SEC Filings (USA)
- Companies house (UK)
- Companies register in Germany
- MarketWatch – provides breaking news coverage of the global financial markets and various economic data for companies, including stock quotes, charts, analysis and SEC filings
- European Union business register
- Japan Exchange Group
- Corporation Search database in Mainland China
- Sovereign Wealth Fund Institute – list of 63,575 company profiles in Asia
Data in government databases
These data repositories maintained by national governments cover different topics such as health, environment and education.
- Data.gov – The USA's leading data portal. It contains datasets across different topics such as: agriculture, climate, energy, health, transportation and crime to name only a few
- Eurostat – Eurostat is the statistical office for the EU that provides access to extensive data on the economy, population, environment, trade and social issues across EU member states.
- Statistics Canada – Canada's national statistical agency
- Australian Bureau of Statistics – provides access to a wide range of statistical data, surveys and publications on Australia's population, economy, labor market and social trends
- National Institute of Statistics and Census (INDEC) – publishes statistical information on demographics, economics, social indicators and more in Argentina
- UK Data Service is the UK's largest collection of economic, population and social research data
- Statistics Korea – provides statistical information and data on population, economics, industry, society and other areas in South Korea
- Central Statistical Office of Poland – provides statistical publications, databases and analytical reports covering Poland's demographics, economics and social indicators
- Statistics New Zealand – publish insights and data about New Zealand
Previous data breaches
Data breach websites aggregate breach data from various sources, including darknet sources. This informs users about breached accounts, leaked credentials and other security incidents.
Here are the top data breach websites:
Cybersecurity threat intelligence data
Threat intelligence—also known as "cyberthreat intelligence" (CTI) is used by organizations to prevent and mitigate cyberthreats against the organization's IT environment. There are different CTI sources to acquire such intelligence:
- CISA Automated Indicator Sharing (AIS)
- FBI InfraGard
- National Cyber Security Centre (NCSC) (UK)
- Australian Signals Directorate (ASD)
- SANS Internet Storm Center (ISC)
- VirusTotal
- ThreatMiner
- Open Threat Exchange (OTX)
Regulatory and compliance data
Compliance data refers to all laws and industry standards that an organization must adhere to legally and ethically. Here are the main sources for getting such information – please note the type of regulations depends on the organization's type of work and/or its location.
- Occupational Safety and Health Administration (OSHA) – provides safety and health regulations for businesses operating in the USA
- Environmental Protection Agency (EPA) – provides environmental regulations and compliance assistance for companies working in different industries
- Federal Trade Commission (FTC) – Provides consumer protection and competition regulations for businesses in the U.S.
- Health Insurance Portability and Accountability Act (HIPAA) – publish guidelines for protecting patients' health information
- Payment Card Industry Data Security Standard (PCI DSS) – provides regulations concerning credit card payments
- Institute of Internal Auditors (IIA) – publish guides for internal audit best practices
Historical performance data
Historical performance data points to past records and indicators that provide insights into an organization's past performance across various areas of its business activities. This data can be obtained from various sources, such as:
Internal systems and records
- Financial statements and reports
- Government databases and public records
- Customer feedback
- Some public websites to get such information include Data.gov and Eurostat
Previous incidents data
Previous incident data is commonly collected from an organization's internal system, such as:
- Internal incident reports and logs of past incidents
- Compliance reports
- Industry incident databases, such as:
- Chemical Safety Board (CSB) Incident Database
- Occupational Safety and Health Administration (OSHA) Inspection Data
- Marine Accident Investigation Branch (MAIB) Accident Database (UK)
- Privacy Rights Clearinghouse – provides information about previous data breaches
- Thalesgroup – provides information about previous data breaches
Social media platforms information
Social media platforms provide a plethora of information for planning and managing business risks. For instance, social media intelligence (SOCMINT) can be used to:
- Monitor brand mentions
- Identify emerging trends and threats; for example, track competitors' activities
- Monitor employee social media activity to detect unauthorized disclosure of sensitive company information
Different tools and online services can be leveraged for collecting SOCINT, such as:
- Google Alert – sends you an email alert once your defined keyword appears anywhere online
- Social Searcher – free social media search engine
- Hashatit – search different social media at once for a specific keyword or hashtag
- Snap Map – for viewing geotagged posts shared by other users worldwide
News articles and blogs
News articles allow businesses to stay informed about the latest news and threats pretending to their industry or area of operations. For instance, by monitoring news articles and blogs, a business can:
- Identify potential risks before they directly impact business operations
- Understand public opinion about the product or service your business is offering
- Identify emerging threats such as data breaches, environmental issues, or product recalls and act instantly
- News articles and blog posts commonly provide detailed analyses of threats and suggest mitigation strategies that can be used to help an organization plan its risk management
Here are some news search engines:
- Bing News
- MagPortal – search for magazine articles
- Google News
- Cornell University Library – provides links to various news databases
Develop search strategies
After identifying the major data sources we will use during our search, we need to specify the search strategies. We can use Google Dorks to fine-tune our search results and return more specific results.
We can use a Large Language Model (LLM) such as ChatGPT to generate advanced Google search queries for us automatically – also known as Google Dorks (see Figure 1).
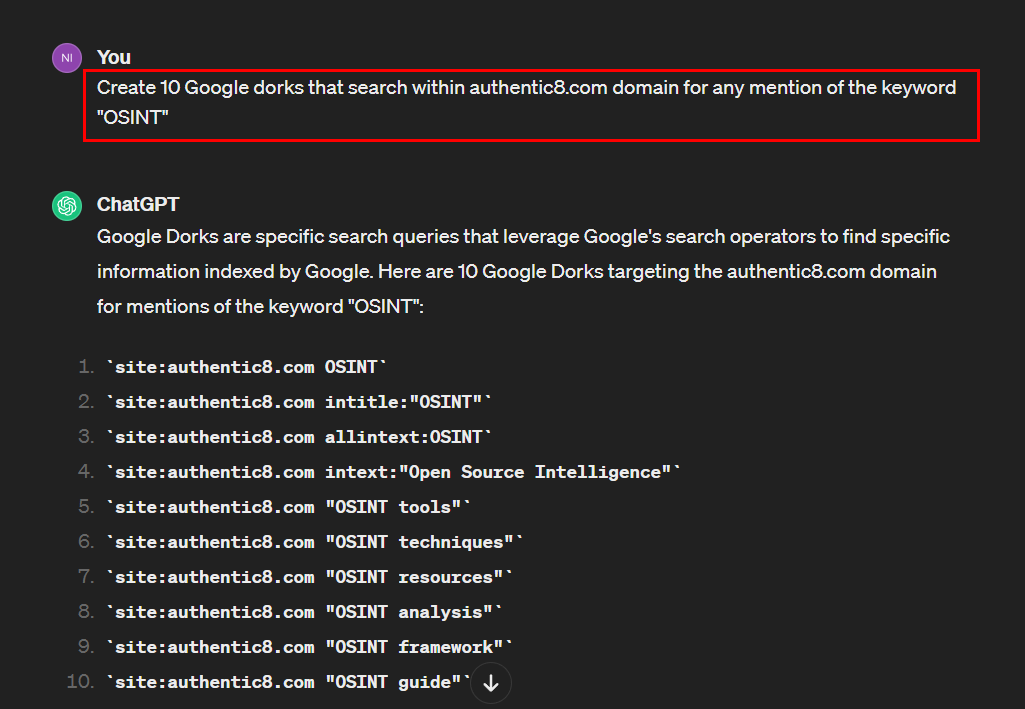
Figure 1 - Use ChatGPT to generate Google Dorks
Assess and interpret data
After gathering all the required information, we need to evaluate the reliability and authenticity of the information. It is better to cross-reference the collected information with other reliable sources.
There are numerous tools to aid OSINT in interpreting and visualizing gathered data, such as:
- Gephi
- NodeXL
- IBM Watson Tone Analyzer – for sentiment and emotion analysis
Finally, we draw conclusions to get actionable insights from the available information.
Investigate safely
Professional researchers rely on managed attribution to control their digital fingerprint and appear in-region to foreign websites. To learn more about how to conceal your identity and protect your information, read more about Silo for Research or start a trial.
Tags Anonymous research Cybersecurity Financial crime Phishing/malware Secure web access SOC

